Introduction
In this post I will explain how to replace an existing application’s configuration profile, sign it, and deploy that application to a device.
By generating a new configuration profile you can specify certain things like which devices the application is allowed to run on and whether it is allowed to run in debug mode.
You can take an existing application and configure it to run on your own device in debug mode, which is useful for runtime analysis.
Get the IPA file
You will be using the UnCrackable-Level1.ipa from the OWASP MAS iOS Crackmes which can be found here
curl -L https://github.com/OWASP/owasp-mastg/raw/master/Crackmes/iOS/Level_01/UnCrackable-Level1.ipa -o UnCrackable-Level1.ipaGenerate a new configuration profile
Create a blank iOS project in Xcode.
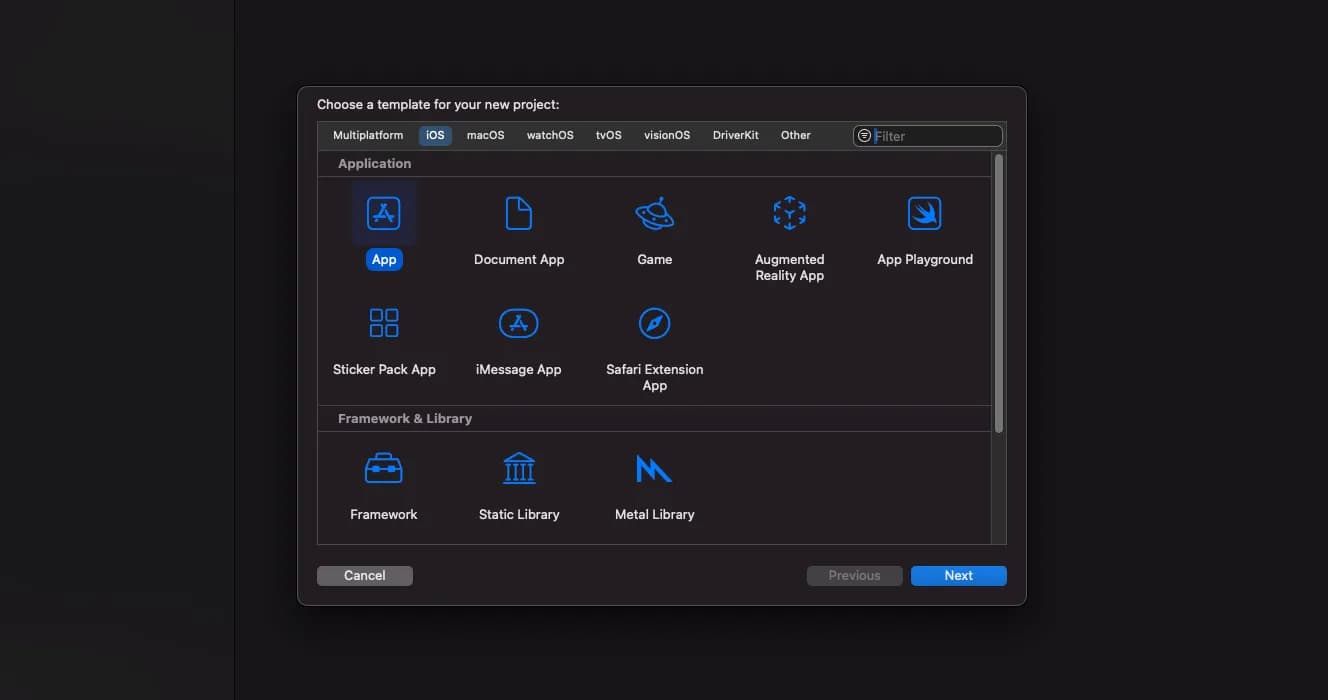
Take note of your Bundle Identifier - you will need this later.
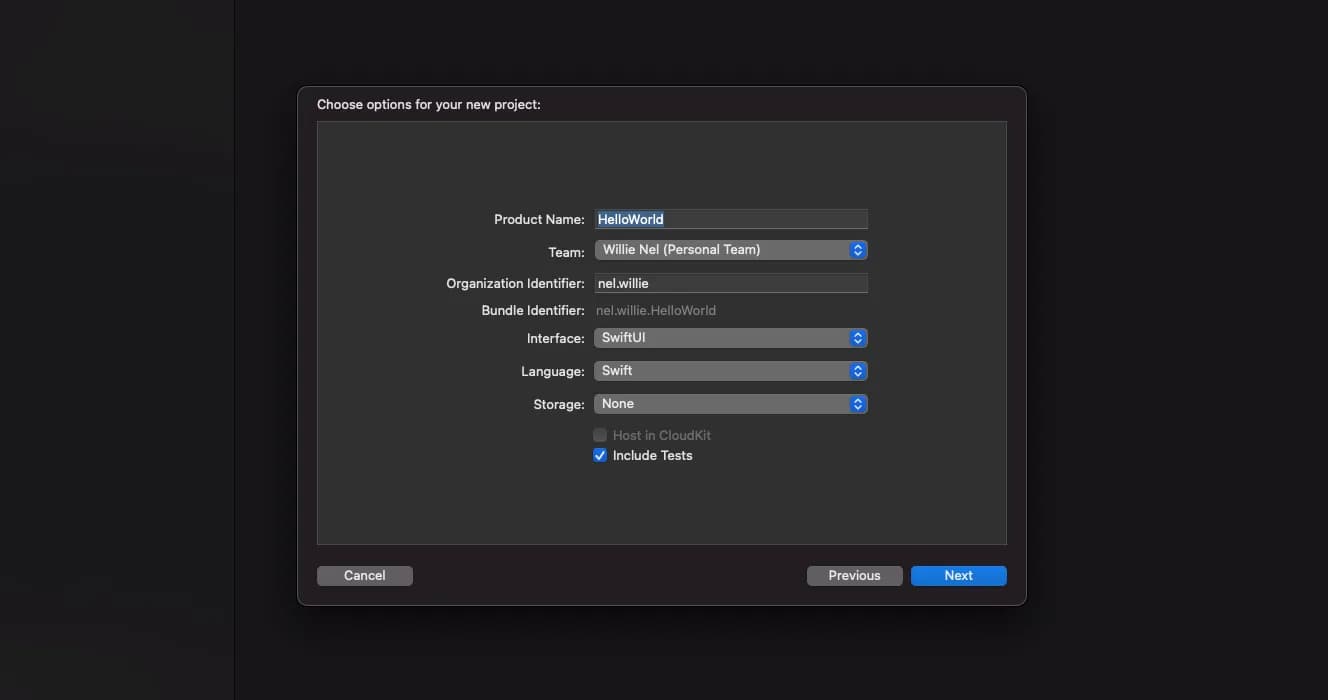
Select your device as the Run Destination
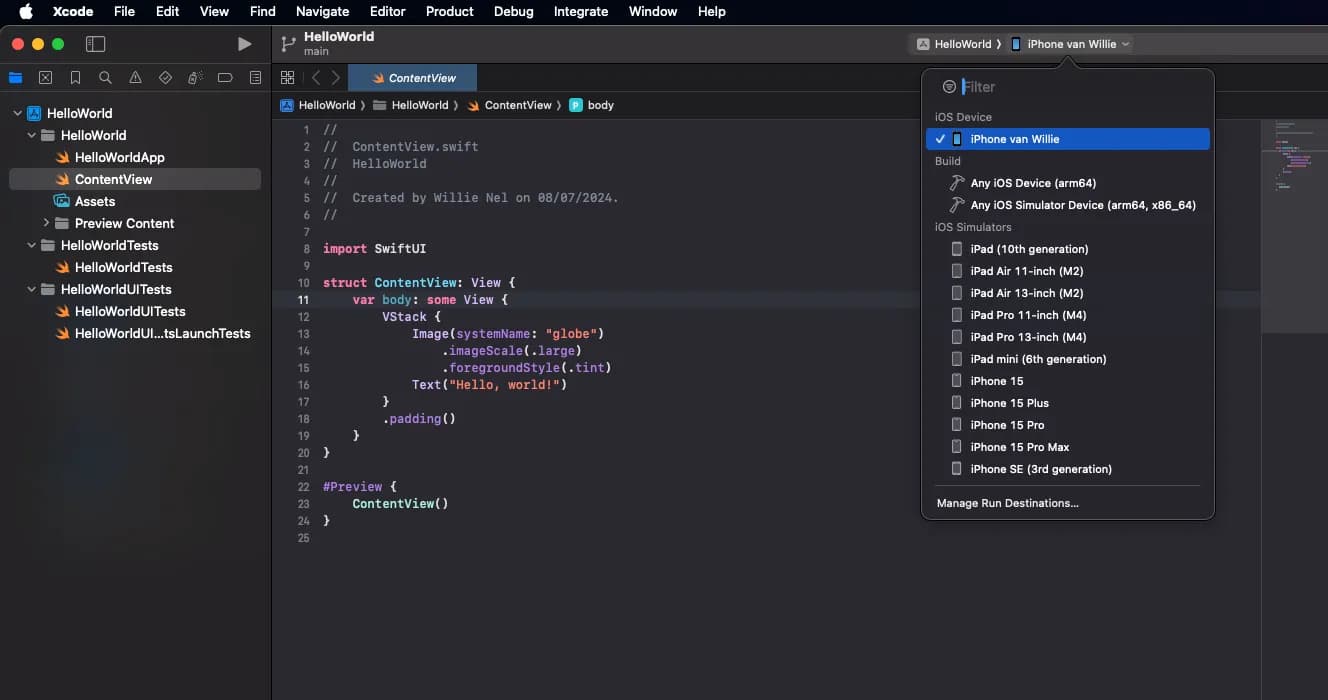
Build your project
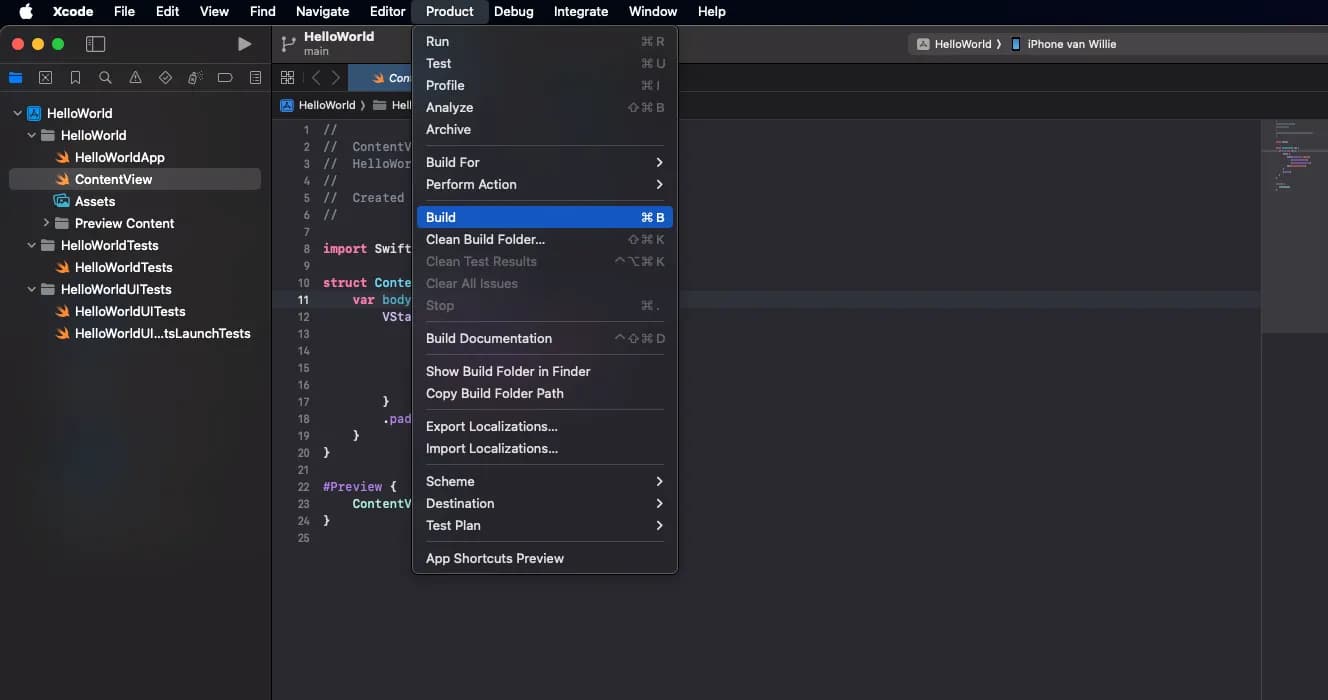
After a successful build you can copy the configuration profile - remember to replace YOUR_PRODUCT_HASH with the value on your filesystem.
cp ~/Library/Developer/Xcode/DerivedData/HelloWorld-YOUR_PRODUCT_HASH/Build/Products/Debug-iphoneos/HelloWorld.app/embedded.mobileprovision .View the contents of the file and make sure that it contains the correct bundle identifier that you entered during project creation.
security cms -D -i embedded.mobileprovisionTake note of the application-identifier value - this should contain a hash appended to your bundle identifier.
<key>application-identifier</key>
<string>Z4CUW8W5KV.nel.willie.HelloWorld</string>Sign the application
To sign the application you will use a tool called node-applesign which can be found here
The switches for this command:
- -c: Clone the entitlements from the configuration profile to the application
- -b: Change the bundle identifier when repackaged
- -m: The configuration profile to use
applesign -c -b "nel.willie.HelloWorld" -m embedded.mobileprovision UnCrackable-Level1.ipaThis will produce a file called UnCrackable-Level1-resigned.ipa
Verify the application
In order to verify that the application was signed correctly you can unzip the resigned IPA file.
unzip UnCrackable-Level1-resigned.ipa
#Archive: UnCrackable-Level1-resigned.ipa
# creating: Payload/
# creating: Payload/UnCrackable Level 1.app/
# creating: Payload/UnCrackable Level 1.app/_CodeSignature/
# ...You can then read the contents of the configuration profile the same way you did earlier.
security cms -D -i Payload/UnCrackable\ Level\ 1.app/embedded.mobileprovisionTo quickly verify if both files are the same you can use the diff command.
diff embedded.mobileprovision Payload/UnCrackable\ Level\ 1.app/embedded.mobileprovisionIf there is no output in the terminal it means the two files are identical.
Deploy the application to your device
To deploy the application you will use a tool called ios-deploy which can be found here
The switches for this command:
- -W: Ignore WIFI devices - if you are using a USB device
- -b: Path to the application that needs to be installed
ios-deploy -W -b UnCrackable-Level1-resigned.ipa
# [....] Waiting for iOS device to be connected
# ...
# [ 9%] Copying Payload/UnCrackable Level 1.app/embedded.mobileprovision to device
# ...
# [ 52%] CreatingStagingDirectory
# [ 57%] ExtractingPackage
# [ 60%] InspectingPackage
# [ 65%] PreflightingApplication
# [ 70%] VerifyingApplication
# [ 75%] CreatingContainer
# [ 80%] InstallingApplication
# [ 85%] PostflightingApplication
# [ 90%] SandboxingApplication
# [ 95%] GeneratingApplicationMap
# [100%] InstallComplete
# [100%] Installed package UnCrackable-Level1-resigned.ipaThe application will now show up on your device.

When you tap on the icon it will launch the applicaiton and display the home screen.
Trust developer and verify application (Optional)
Depending on your configuration (Apple Developer Account vs Personal) you might have to trust the developer and verify the application on the device.
An excellent article that explains how to do this can be found here
Final thoughts
Now that I have a working application that can run on my device in debug mode I can perform runtime analysis on it.
In a future post I will cover configuring objection for iOS runtime analysis.